The types of network topologies and their characteristicss make up the physical map of a network, which allows them to exchange data and information. In this article you will be able to learn more about this interesting topic.

Types of network topologies and their characteristics
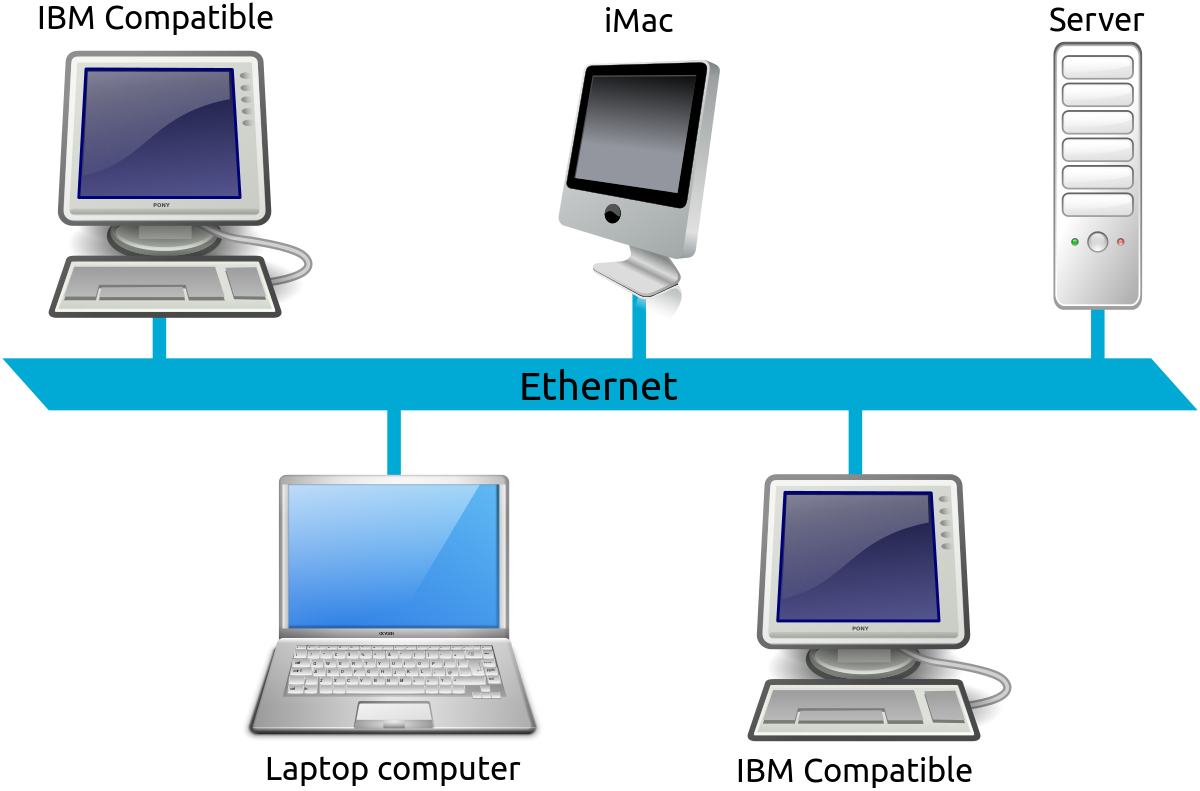
When talking about this topic in the computer world, reference is made to the structure and architecture of the physical and logical map by which developers and programmers use to exchange data through a network system.
The types of network topology and their characteristics have a utility that allows various nodes (computers, printers, servers, hubs, switches and routers) to be connected to each other, in order to send data and information to each one.
It is composed of the so-called physical topology, it is the way in which the cables called media are interconnected, between the nodes, and the logical topology where the way in which the hosts access the media is defined. See how Build a network cable
To put it in other terms, it is the way in which a network is designed. This concept has to do with the organization and connection of the devices and equipment that allow the transmission of data and information to specific places.
There are many types of network topologies and their characteristics, which make each one the conformation of a system different from another. This field is carried out by various programmers who must know various codes and manage a specific computer digital language.
The conformation, the type of network topologies and their characteristics allow to establish how to connect the internet service from the provider and its way of transmitting through the router. The topology allows establishing the way in which transmissions should be managed and where they will be directed.
The design allows the switch to be connected to another switch or router, which can lead to a host or workstation. This creates a kind of tree-like branches, it is then appreciated how the first router transmits to the rest of the devices through channels.
Various network topologies can be developed by establishing a basic architecture, which is almost always related to the interconnection between nodes. The distance between them determines the transmission or media channels. However, each element makes up the physical interconnections, the transmission rates and the signal can sometimes affect the efficient operation of the network.
The components that make this action possible are the server network, the network devices, the terminals and the channel through which the data travels called communication media. These components allow to structure an architectural map of the network system, which is called network topology. We will then see the types of network topology and their characteristics below.
What are the topologies?
In the world of networks, programmers and developers consider only eight types of network topology and their characteristics when planning and structuring networks. These are tree or hierarchical, bus, ring or circular, star, mesh, and Point to point, let's see.
Tree, hierarchical or tree
This type of topology is seen as a collection of networks in the shape of a star but very organized. Depending on its hierarchy, the construction is established based on the individual peripheral nodes called leaves. The nodes transmit and receive data from another node and do not handle repetitions. Very different from other topologies where they are only responsible for distributing.
The individual nodes are isolated from the network through a fault that is caused in the connection path of the node itself. The failure allows isolating the leaf node, but if the complete link fails, the section may be isolated causing some type of transmission cutoff.
This generally happens due to excess traffic, so it is important to develop central nodes that help maintain a menu of information different from those connected to the network. A network structure is then formed that transmits data packets to all nodes, allowing it to be used as connectors.
Bus
Also called "common conduit", "linear" or "line", it is one of the most interesting variants that exists in the types of network topologies and its characteristics, it is considered one of the easiest to develop. The structure consists of a PtP communication channel that connects users and constantly associates them between two endpoints.
It works similar to the so-called tin phone that children use to play and communicate. When the telecommunications system is carried out in a switched way, a permanent circle is established. In understandable terms, it works similar to a telephone, when it is programmed only to make calls to a specific number and permanently.
This communication remains until needed, it can be released when required. It is like dismantling the communication of a system, after it has carried out a task and is then disconnected.
Ring, circular or ring
It is a network that allows you to organize and order networks in a more stable way. Each node connects with other nodes forming a single transmission and communication. Then a unique path is also formed between the nodes allowing to handle individual data packets.
The ring topology can be unidirectional even though there is traffic in both directions or turning in a circular way, creating a kind of ring. It can also be structured in a bidirectional way, where the ring allows to provide a single path between two nodes.
These transmission paths can sometimes be interrupted if some of the nodes have a problem. Among the advantages is that each device has access to the token, having the opportunity to transmit without problems.
It does not require a central node to manage connectivity between computers. It also allows devices to configure a system of Virtualization only by removing the cable.
Estrella
The types of topologies and their characteristics allow them to offer a variety of configurations based on the needs of the user or company. In this case, the star topology or star as it is also called, limits the possibility of a network collapsing. This is done by connecting all nodes to a central node.
This central node sends the transmissions it receives to any peripheral node and to all the nodes that are in the network. The peripheral nodes communicate with each other, transmitting only from the central node. If there were a fault in the connection line of any node, the central node would only cause its own isolation
The only problem is that the central node is recharged supporting a considerable amount of traffic. For this reason, this type of structural network topology is recommended in small systems and not in transmission systems that generate amounts of traffic and a lot of volume in sending and receiving data.
Mesh
This network topology is a form of connection similar to the previous one where each node is connected to all nodes. It allows to carry messages from one node to another through various channels. When the mesh network is fully connected, there is no interruption in communication. It also allows each server to establish its own connections with the rest of the servers.
The advantage in this type of network topology and its characteristics is that it is not structured through a central node, this creates a forecast in which the failures are limited. Allowing maintenance for longer periods. Another advantage is that if the connection disappears, it does not affect the network nodes.
The mesh network is very reliable, reduces redundancy, and confidence is tolerant of higher failures. One of the disadvantages of this type of network topology is that they are a bit expensive to install. They require interconnection of each of the nodes with the rest of the nodes.
This allows to increase the interfaces greater than those that each one must have. That is why it is important to structure the topology based on the wired or wireless connection. The redundancy of the routes to the same destination reduces the frequency of occurrence of failures.
One of the disadvantages results in the increased cost of installation can be high when trying to establish the network through cables. What they lead to implement the use of a greater amount of resources among those that it turns out to know How to connect to a network to find a more profitable structure.
Point by point
Also called "Point to Point Protocol" or "Peer-to-Peer", it represents the types of network topologies and their characteristics, which use long-range networks (WAN), the chaining algorithms are somewhat complicated. The errors are corrected in the intermediate nodes and in the ends.
Point-to-point networks are those that respond to a type of network architecture in which each data channel is used to communicate only two computers, in clear opposition to multipoint networks, in which each data channel can be used for communicate with various nodes.
Network devices act similarly and in pairs with each other. Each device takes the role of emitter or receiver. The complexity of this system allows you to establish independence in a message request. The roles are usually reversed and the receiver becomes the sender.
The stations receive only the messages emitted by the nodes of the network. They identify the receiving station according to the sending address. The connections between the nodes are made with one or more transmission systems. These can send them at different speeds, allowing them to work in parallel. Intermediate nodes can generate traffic based on the type of message they send.
The delays are due to the transit of the messages through the intermediate nodes. The cost of installation depends on the number of cables needed for the main connection and the number of links between the connections.