The technique is called 'Steganography'and consists of write hidden messages in such a way that no one, except the sender and the receiver, suspects the existence of the message. Well, that is exactly what it offers us DeEgger Embedder, a utility that in this case will help us hide files within others and thus share them with extreme security keeping our privacy safe. Remote and unnoticed in the sight of third parties, which is what you are looking for.
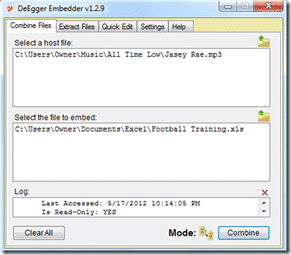
DeEgger Embedder It is only in English, but its use is simple as I will comment on the following image. There are 3 basic steps to follow, let's see then:

- Select a host file: Here we will have to drag to its interface or load with the indicated button, the false file that we are going to generate. It can be of any format, a simple image or an mp3 for example.
- Select the file to embed: The process is the same as the previous point, with the difference that here we will load the 'secret message', that is, the file to hide.
- Combine: One click on this button and a fake file which is shown exactly the same as the one we have loaded in the host file. Common and ordinary, nothing suspicious for anyone, but for us a file with its little secrets that only the sender will see.
It is worth mentioning that the tool has several camouflage modes, to be configured in the tab Settings or right click on Fashion.
Now, on our part, the camouflage work is done, now the sender will be able to unhide the secret file using the same program, but this time from the '' tab.Extract files'. As simple as that.
DeEgger Embedder is a free privacy tool, its installer file is just over 600 KB and is compatible with Windows 8, 7, Vista, XP.
Official site: DeEgger Embedder
Download DeEgger Embedder